Video Conferencing: 2) Confidence
“Can you hear me now?”
Conference calling has always been around; however, no one is ever confident whether it is working as intended. All-time-favorite questions for conference calls are still “Can you see my screen?” or “Can you hear me now?”—which usually result in a very quick answer from the audience because it’s obvious (to them, at least). However, if the question was whether “unauthorized” people could see and hear what you’re sharing and saying, what would you say? Could you confidently answer that question? What if it was not just one meeting currently in session, but multiple previous meetings that were recorded and shared across a company?
The Invisible Essentials
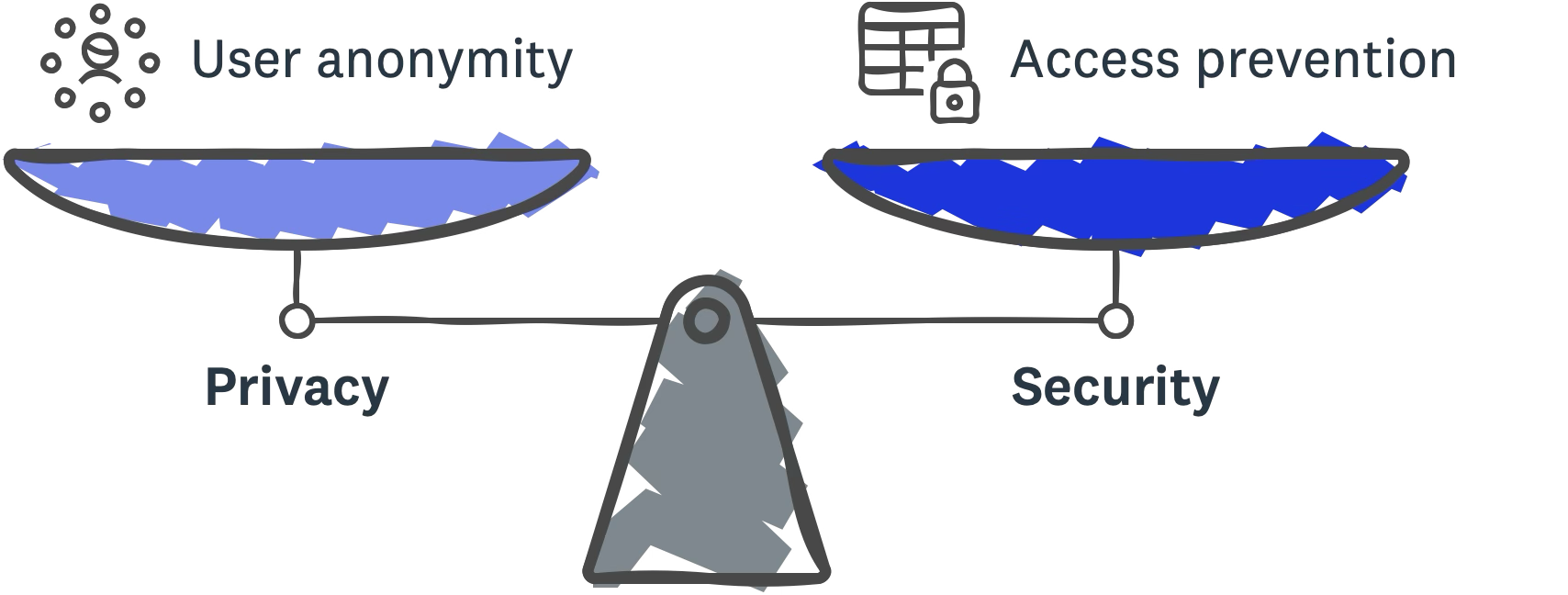
Privacy and Security are important features of video conferencing even though you cannot “see” them. At the risk of oversimplification, privacy is focused more on keeping the user’s identifiable information anonymous to everyone at the service except for a select few. Security is focused more on the service preventing unauthorized access to data, which may include user data. These two aspects are crucial for video conferencing because they help create a sense of openness so we can freely talk about our work, our teams, and ourselves without worrying about it being exposed to eyes and ears it was not meant for.
However, Privacy & Security often come at the expense of ease-of-use. One of the big issues that has come up for Zoom has been its lack of end-to-end encryption, which it claimed to support but was later found to be Transport Layer Security. This meant that things were only encrypted in transit, and Zoom could access your info when it arrived at its servers. Zoom complied with its customers’ requests for end-to-end encryption, but it came at the loss of the ability to dial in from phones and the added need to give Zoom some personal information, especially for the free tier. As Zoom may no longer know who is in the calls, it needs a minimum amount of identification, such as a phone number. Microsoft Teams has built a robust Secure Real-time Transport Protocol for video, audio, and desktop sharing, but the encryption (and corresponding keys) are owned entirely by Microsoft, which means a loss of control for its customers.
Open-Source and VR
Some prefer ownership to be shared with the community rather than a commercial organization. Jitsi Meet is an open source application that’s moving towards end-to-end encryption and its building blocks are created by a vibrant community that’s more interested in personal and communal reputation than monetary gains. It requires a different company mindset to nurture an open-source culture for its products and for users to feel protected.
More immersive technologies, such as Oculus VR, make communication more effortless by revealing more of our body language, a useful cue for when to share certain information with others. With this enhanced communication, however, comes a few unique security concerns. Virtual reality headsets can collect biometric data that some fear could be used for nefarious purposes, such as denying a person auto insurance if data indicates they have a slow reaction time. Additionally, Oculus has future plans to require a Facebook account in order to use the headset, forcing users to tether their data to a company with a reputation for extensive data mining. Sales of Oculus headsets have been halted in Germany because of these very privacy concerns. Cameras on the outside of the headset, used to map a person’s movement, can also map the interior of their homes.
The Weakest Link
These examples show how difficult these payoffs and tradeoffs are, especially given the plethora of video conferencing tools to choose from as many companies join this gold rush. Unfortunately, in areas of Privacy & Security, the weakest link is usually not the network, application, device, or data storage—it’s usually people. Privacy features such as waiting rooms, renaming, and password protection were made available, but people did not use them. Thankfully, Zoom has now moved towards Smart Defaults, which turn those security features on by default and make them easily accessible from the application. This means the user is protected by default but still has control over those discrete features, which is a nice balance of payoff and tradeoff. Compare this to Microsoft Teams, where a simple name change requires a request from your administrator. It could be argued that it’s more secure, but it comes at the cost of less control for the user and additional, unnecessary tasks for an administrator.
All these Privacy & Security features exist to protect us during video conferencing so that we can be more open about what we’re discussing and sharing. Whether it’s a doctor’s teleconference call or a work meeting, we believe this openness helps us connect with one another.
Are you still concerned about security and privacy? Let’s connect and discuss!